Implementing Secure User Authentication with OpenID Connect and OAuth 2.0

Devising Secure User Authentication in Enterprise Systems: An Expert’s Guide to Implementing OpenID Connect with OAuth 2.0
In today’s digital landscape, securing user authentication is paramount for any enterprise system. OpenID Connect, when effectively combined with OAuth 2.0, offers a robust solution. Let’s delve into the intricacies and advanced strategies for implementing these protocols to safeguard your enterprise systems.
Understanding OpenID Connect and OAuth 2.0
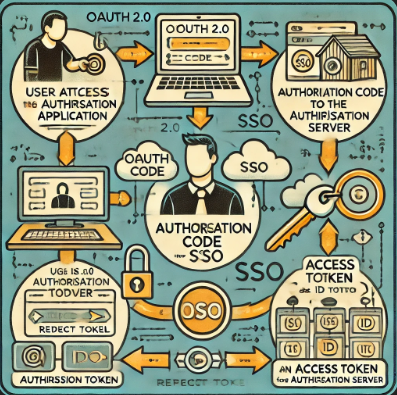
OpenID Connect is an identity layer built on top of the OAuth 2.0 protocol, which is primarily used for authorization. By leveraging OpenID Connect, enterprises can authenticate users effectively, ensuring both security and user data privacy.
- OpenID Connect: Adds a token (ID Token) that explicitly handles authentication.
- OAuth 2.0: Provides a framework for token-based authorization, allowing third-party applications to access user resources without sharing passwords.
Key Considerations for Implementation
- Token Security: Protecting the integrity and confidentiality of tokens is crucial. Use JSON Web Tokens (JWT) for secure token structure and ensure they’re signed (using RS256) to verify authenticity.
const jwt = require('jsonwebtoken'); function generateToken(payload, secret) { return jwt.sign(payload, secret, { algorithm: 'RS256' }); }
- Flow Selection: Select appropriate OAuth 2.0 flows based on your architecture:
- Authorization Code Flow: Best for server-side applications, offering enhanced security.
- Implicit Flow: Suitable for client-side (browser-based) apps, though with security trade-offs.
- Hybrid Flow: Combines both, allowing more flexibility.
- Scopes and Claims Management: Define scopes clearly to limit access and use claims to convey user information securely. Over-privileging scopes can lead to increased risk.
- Refresh Tokens: Include refresh tokens to obtain new access tokens. Implement secure storage practices and expiration handling to mitigate misuse.
function refreshAccessToken(refreshToken) { // Example API call to refresh token endpoint }
Advanced Insights
- Token Revocation: Implementing token revocation endpoints can further bolster security by allowing the immediate invalidation of tokens.
- Data Liaison: Consider integrating with existing directory services through connectors to streamline identity management and reduce duplicate information sources.
- Monitoring and Auditing: Regularly audit authentication activities and maintain logs for anomaly detection and compliance adherence. Automated monitoring tools can provide real-time insights into potential breaches.
Best Practices
- Implement Mutual TLS: To enhance security, mutual Transport Layer Security (TLS) should be employed during token exchange to ensure both client and server are authenticated.
- Leverage Existing Tools and Libraries: Utilize open-source tools like Keycloak or libraries like
openid-clientto streamline implementation and ensure compliance with established standards. - Cross-Protocol Compatibility: Ensure that your implementation is compliant with both OpenID Connect and OAuth 2.0 standards to maintain interoperability.
By following these advanced strategies, enterprises can ensure that their user authentication systems are secure, scalable, and reliable, leveraging OpenID Connect and OAuth 2.0 to their full potential.